Qualified electronic signature: ECJ ruling of February 29.02.2024, 25 A current ECJ ruling specifies the interpretation of Article XNUMX of the Regulation (EU)...
Signature creation

FAQ & Tips
Check our FAQ for problems and questions.

Frequently asked questions on the following topics
intarsys products
Partner products
General topics
intarsys products
General (install, license...)
c
Expand all
C
Fold everything in
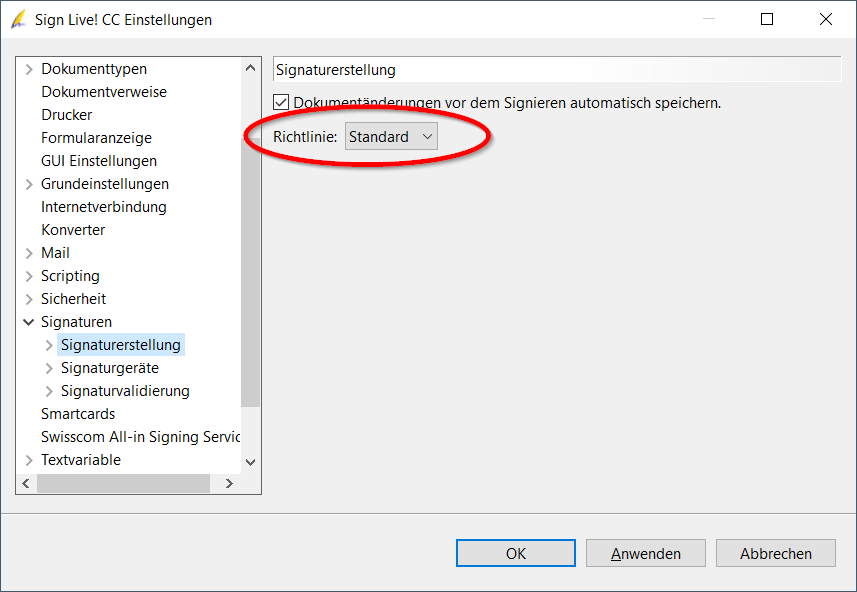
Since January 1.1.2024st, XNUMX, Sign Live! CC in the signature process when using certain algorithms that they have expired. The background is that the signature creation settings are set to the outdated “SigG” testing standard.
Workaround: Reset this setting to “Standard”. Then the error should no longer occur.
If the problem persists, please send a description of the error and the current log file an support@intarsys.de.
The warning in the SLCC settings pages (Tools > Settings > Signature Devices > …) still appears.
The problem has been completely resolved by using the corrected version of Sign Live! CC 7.1.11.3 (for download) or from 7.1.12.
Published to
2 January 2024
What does Sign Live! CC implements the valid catalog of algorithms"?
An algorithm catalog defines which cryptographic algorithms are currently and for a future period considered secure. In doing so, it largely defines the security level of a PKI(1).
Until June 30.06.2017, 01.07.2017, the Signature Act and the Signature Ordinance (SigG/SigV) defined a PKI for qualified electronic signatures and required an algorithm catalog that was constantly updated. Since July XNUMXst, XNUMX, this has been done throughout Europe in the eIDAS regulation regulated.
The BSI (Federal Office for Information Security) creates the algorithm catalog based on a 7-year forecast. This means that the algorithms under consideration can be considered safe today and will most likely continue to be safe for at least the next 7 years. Very often these periods are extended every year. If it is expected that an algorithm will become unsafe, users have a warning period of 7 years. It has not happened since the existence of the SigG algorithm catalog that known attacks suddenly endanger the security level of crypto algorithms so much that a validity period had to be shortened.
Sign Live! CC implements the specifications of the algorithm catalog valid at the time of publication of the software.
What happens to the algorithm catalog through the implementation of the eIDAS-VO?
To the eIDAS regulation implemented in Germany, SigG/SigV will be replaced by the Trust Services Act and the associated ordinance at the end of 2017. An algorithm catalog is e.g. Currently not anchored in the eIDAS-VO. It is still unclear whether the EU administration will decide on the necessary rules at EU level by then or whether Germany will continue to stick to the German catalog as long as there is no EU catalogue. We will keep you informed on this topic.
(1) PKI = Public Key Infrastructure. For detailed information see https://de.wikipedia.org/wiki/Public-Key-Infrastruktur
Published to
August 24, 2022
In rare cases it happens that Sign Live! C.C.C or Sign Live! cloud suite bridge not start after the installation and that the following error message appears with possible error causes:
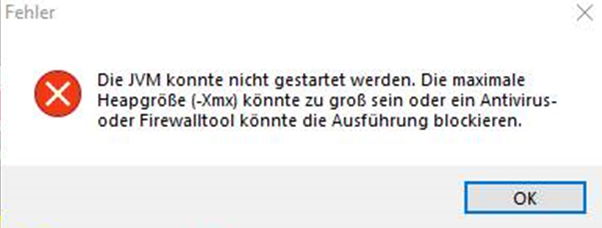
Practice has shown that the causes of error listed in the error message often do not lead to a solution to the problem. Another possible cause is that a required Microsoft Visual C++ runtime library is missing or outdated.
This runtime library is available in the Microsoft Visual C++ Redistributable package.
Please check the Windows settings under "Apps and Features" to see whether the current version of this software package is available on your computer.
Es wird at least the package with the Year number 2015-2019 or a newer version is required.
If this package is not available or is an older version, please update and then restart the intarsys application.
The current versions of the software package can be found at:
https://aka.ms/vs/17/release/vc_redist.x64.exe (for the 64 bit version of the application)
https://aka.ms/vs/17/release/vc_redist.x86.exe (for the 32 bit version of the application)
Published to
March 21, 2023
The standard configuration for the SLCC application log is stored under
\classes\config\logback.xml
The “FILE” appender is responsible for the SLCC application log.
So adjustments have to be made there.
To customize the location/number/size of log files to be created, change <file> and / or <rollingPolicy>.
You can find information on this under http://logback.qos.ch/manual/appenders.html.
To customize the layout of the log file, change this <pattern> according to your needs.
Information on the variables used in it can be found under
http://logback.qos.ch/manual/layouts.html
% p /% le /% level are e.g. B. for the level designation.
Published to
August 21, 2022
When reinstalling Sign Live! C.C.C or when changing computers, it can be helpful to adopt settings from an existing installation.
The settings of Sign Live! C.C.C are stored in the profile directory of the application.
- (Windows client:
C:\Users\<user>\.SignLiveCC_<major>.<minor>) - (Windows server:
C:\ProgramData\.SignLiveCC_<major>.<minor>)
The following subdirectories can be adopted:
"preferences" (includes settings made via "Extras > Settings")
"instruments" (includes configurations of service containers, signature pools, timestamps, configurations for signIT gears, etc.)
"licenses" (may include the license)
"db" (should be adopted if own certificates are stored in the certificate store of Sign Live! C.C.C were imported)
A quick guide to migration is available as a Tutorial ready for download.
Published to
18 January 2023
Variables are used when Sign Live! C.C.C using the bin\SignLiveCC.exe.vmoptions file. These are defined using the "-Dproperty = value" option and a value is set. Environment variables can also be specified as values.
Examples:
-Dmy.test = test -Dmy.profile = $ {USERPROFILE}
These variables can be used, for example, when configuring Sign Live! C.C.C via ${properties.my.test} or ${properties.my.profile}.
For more information on using the vmoptions file, see the Users Guide from exe4jused to create the Sign Live! C.C.C Launcher for Windows is used.
Published to
August 21, 2022
Should several Windows services from Sign Live! C.C.C are operated in parallel, a name must be specified when installing the service. To do this, customize the bin/SignLiveCC_service_install.bat file by specifying a name after the /install option.
For example:
……./install MySLCCService
The same name must be specified in the bat files for starting, stopping and uninstalling the Windows service.
Parameters for use in Sign Live! C.C.C Windows services are passed using the file “bin/SignLiveCC_service.exe.vmoptions”. Further information can be found here.
Published to
August 21, 2022
In some circumstances it makes sense to use instead of Sign Live! C.C.C to use your own JVM.
For example, if you access the via JMX Sign Live! C.C.C Want to access MBeans or the application remotely debug want.
Follow these steps:
- Name the directory with Sign Live! C.C.C delivered JVM.
Windows: C:\Programs\SignLiveCC_7.1\jre --> C:\Programs\SignLiveCC_7.1\jre_off
Linux: /opt/intarsys/signlivecc-7.1.7/bin/jre --> /opt/intarsys/signlivecc-7.1.7/bin/jre_off - Windows:
Define the root directory of the JVM to be used via the Windows system settings in the system variable EXE4J_JAVA_HOME (without the trailing "\").
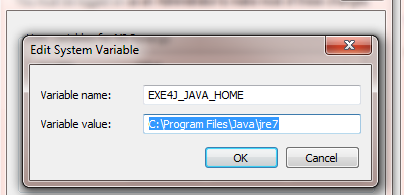
If this does not lead to success, also define EXE4J_LOG=yes to get information about the behavior of EXE4J:
During operation, a message box provides information about where the log is stored.
Linux:
Set $CABARET_JAVA_HOME to the root directory of the desired JVM
(see also information in /opt/intarsys/signlivecc-7.1.7/bin/signlivecc.sh)
3. Start Sign Live! C.C.C new. You should now find the defined JVM in the log under java.home.
Important NOTE
With Sign Live! C.C.C delivered JRE uses the keystore.type = jks.
Separately installed JRE/JDK must be adjusted accordingly.
To do this, set in your Java installation in the file java.security --> keystore.type = jks.
Published to
August 21, 2022
When creating an installation medium for Windows, the software "InnoSetup" from "JRSoftware" is used.
Innosetup supports the "Silent Install" function. Installation parameters recorded once can be used in subsequent installations.
For example:
Create a file with your installation parameters by calling the following command line:
- setup_SignLive_CC_JRE_6.2.1_64Bit.exe /SAVEINF="c:\temp\install.inf"
Adjust the file if necessary and use the saved parameters via the call
- setup_SignLive_CC_JRE_6.2.1_64Bit.exe /SILENT /LOADINF="c:\temp\install.inf"
for further installations.
You can find more call parameters for Innosetup here
Published to
August 20, 2022
We are introducing Sign Live! CC available for different operating systems. For information about the operating systems, please refer to current data sheet. ThinClient scenarios based on Windows Terminal Server or Citrix Presentation Server are also supported.
- Installation on Windows
Step-by-step instructions for downloading the software, installing and licensing can be found as a tutorial here.
- Installation on macOS
The tutorial for installation and licensing under macOS is available here is available for storage, management and analysis.
- Note:
If you have already installed the application in a same version or a previous version or if you are installing a patch:
Exit the application, preferably via the system tray (taskbar), if it is running.
If you have configured the software as a Windows service, stop the Windows service.
Published to
August 20, 2022
How to install the software on a Linux system:
- Download the file with the extension ".tar.gz".
- If you have already installed the application in a previous version or if you are installing a patch:
- Quit the application if it has started.
- If you have configured the software as a Linux service, stop the Linux service.
- Unzip the downloaded file as follows, using the file name of the downloaded file plus the version number as the name for the installation directory:
tar -xf signlivecc_*.tar.gz -C /var/signlivecc-7.1.11/ - Check your installation.
- Start the installed application.
Note: You should also unzip an update into a new directory in order to avoid the contents of different versions in the installation. Specific adjustments must be carried out again or adopted after the installation.
Note: Depending on the product, the file name of the downloaded file will be different. For the example in point 3, the product “Sign Live!” CC” .
Published to
August 20, 2022
A font copied into the fonts directory is not displayed in an intarsys product and cannot be used. What should I do?
Our products read the fonts from the standard directory. On Windows this is C: \ Windows \ Fonts. In the user view, not only the fonts from this directory are displayed, but also the fonts from the user directory. This can only be seen when the properties of a font are displayed.
Copied If you put a font in the directory C: \ Windows \ Fonts, it will be displayed there, but is de facto in the user directory. Our software does not access the user directory by default, so the font is not available even though you see it in the supposedly correct place.
Solution:
- Install the font instead of copying it. Use this to do this context menu (right mouse button) and choose "Install for everyone". This will put the font in the correct directory.
Published to
August 20, 2022
Sign Live! C.C.C
c
Expand all
C
Fold everything in
Since January 1.1.2024st, XNUMX, Sign Live! CC in the signature process when using certain algorithms that they have expired. The background is that the signature creation settings are set to the outdated “SigG” testing standard.
Workaround: Reset this setting to “Standard”. Then the error should no longer occur.

If the problem persists, please send a description of the error and the current log file an support@intarsys.de.
The warning in the SLCC settings pages (Tools > Settings > Signature Devices > …) still appears.
The problem has been completely resolved by using the corrected version of Sign Live! CC 7.1.11.3 (for download) or from 7.1.12.
Published to
2 January 2024
The application runs smoothly. Problems arise only when processing large files. The decisive factor is the size of a file while processing in the application. This is due to the size in bytes and through their structure. Problematic are e.g. E.g. many pages (>100), large images.
The following typical error messages can be seen in the log:
- java.lang.OutOfMemoryError: Java heap space
--> Further information can be found in the FAQ - Providing more RAM - e.g. B. java.net.SocketException: Software caused connection abort: socket write error
--> see below
These problems can occur when using the SOAP protocol.
In this case, limiting settings must be increased.
To do this, create the file /classes/cxf/bus.properties e.g. B. with the following content:
org.apache.cxf.stax.maxTextLength = 512000000
and restart the application.
This increases the message size from approximately 100 MB (default) to 512 MB.
Note that the message size is always larger than the actual file size (factor approx. 64) due to the base1,3 encoding.
Published to
August 21, 2022
When opening very large files, the Sign Live! C.C.C There is not enough RAM available (error message: … “Java heap space”). The log provides information about the maximum amount of memory Java requires from the operating system, e.g. E.g.:
[2019.11.20-09:29:57.818][I][d.i.tools.logging][executor singleton][] maxmemory=477626368First, check that the operating system can actually provide that much memory for Java. Operating system and other applications also require memory!
If enough memory is available, please gradually increase the memory claimed by Java.
So put in Sign Live! C.C.C more memory available:
- Copy the fileINSTALLATION DIRECTORY> \ demo \ vmoptions \ more memory \* .vmoptions1 after \bin.
- Starten Sie Sign Live! C.C.C New.
- If the main memory is not sufficient, the value in the vmoptions file can be edited with an editor and the value can be increased to -Xmx2048m, for example. The maximum value depends on how much RAM is available on your computer.
Important note:
- For operation as a Windows service, the signivecc_service.exe file must also be created with identical content.
1) The name of the vmoptions file depends on the operating system used.
Published to
August 21, 2022
Setting up a PDF printer is required for various actions. This is done in Sign Live! C.C.C "Ghostscript" used.
When installing Sign Live! CC version 7.1.7 – or older – please use Ghostscript 9.53.3 or older.
Do you have Sign Live! C.C.C installed in the current version, the current version of Ghostscript can also be used.
Published to
August 21, 2022
Sign Live! CC starts with the language settings of the operating system.
To get the operating language of Sign Live! CC To manipulate it, you need administrator rights.
Follow these steps:
- Quit Sign Live! CC.
- Use Windows Explorer to switch to the installation directory for Sign Live! CC. This is in most cases
"C:\Programme\Sign Live CC <version>" oder "C:\Programme (x86)\Sign Live CC <version>". - Navigate further into the subdirectory "demo\vmoptions\language english".
- Copy the SignLiveCC.exe.vmoptions file from this directory.
- Change to the “bin” subdirectory of the installation directory Sign Live! CC and drop the SignLiveCC.exe.vmoptions file there.
- Starten Sie Sign Live! CC new so that the language settings are loaded.
By doing this, the entire user interface of Sign Live! CC presented in English.
To reset to German, delete the file “SignLiveCC.exe.vmoptions” from the bin directory and start Sign Live! C.C.C New.
Published to
August 21, 2022
When trust centers switch to a new PKI infrastructure, it may happen that signatures or timestamps created with very new signature cards/certificates are not validly validated. This is due to the fact that the new Trusted Lists (TL) and/or Root CAs (root certificates) were not yet implemented at the time our software was released.
The Update of the trust lists in Sign Live! C.C.C these signatures are validated again.
We will inform you by email as soon as we receive relevant information from a trust center. Each user is responsible for maintaining current certificates.
Via menu item Tools> Certificates> Update Trust Lists trigger the update of the trust lists manually.
If the update is not possible or aborts with an error message, please check:
- The Internet connection
- Whether the virus scanner blocks the updating of the trusted lists
- Whether the firewall blocks the updating of the trusted lists
If the update is still not possible, please send a description of the error and the current log file an support@intarsys.de.
Published to
18 January 2023
Needed to validate signatures Sign Live! C.C.C always current Root certificates that are at least available for the eIDAS-PKI Trust lists (Trusted List-TL).
Sign Live! C.C.C ships with a current set of root certificates at the time of publication. From time to time, trust centers use new root certificates. If we receive information about this from the trust centers, we will forward it to you via email. To do this, register for our newsletter.
In any case, you must ensure that Sign Live! C.C.C updated its root certificates. You can do this manually or automated carry out:
– For the workplace: Manual
This method is completely sufficient for normal installation at the workplace.
- Via menu item Tools> Certificates> Update Trust Lists trigger the update of the trust lists manually.
– For server installation: Automated
Especially in Server installations it makes sense to have the update triggered time-controlled. To do this, adapt the preconfigured service container:
- Via menu item Tools> Services> Service Container Management Configure the schedule of the "Trusted List Update Scheduler" service container and automatically trigger the update of the trust lists:
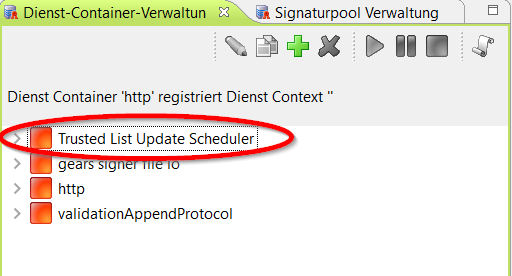
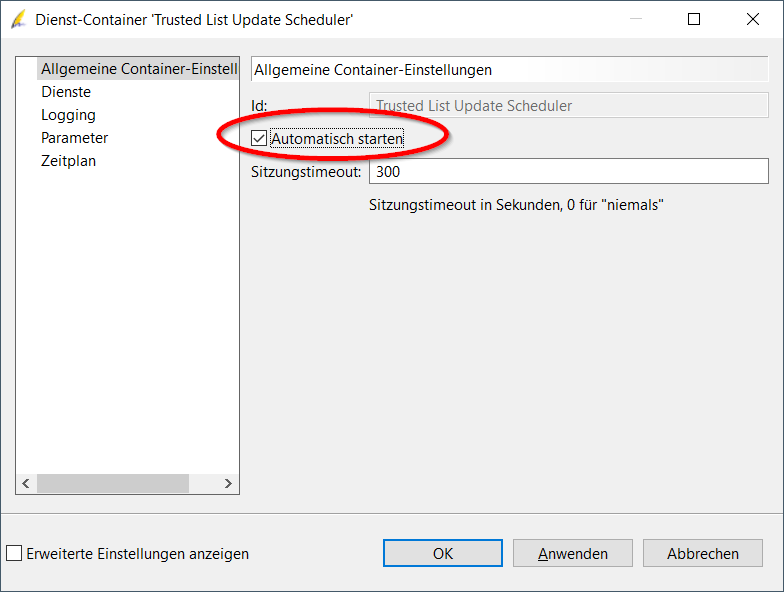
If the update is not possible or aborts with an error message, please check:
- The internet connection (proxy, firewall, ...).
- Whether the virus scanner deletes trusted lists downloaded from the profile directory. The profile directory is where the logs are stored. You can determine this using the menu option Window > Log File.
If the update is still not possible, please send a description of the error and the current log file an support@intarsys.de.
Published to
18 January 2023
In cases where the validating Sign Live! C.C.C-Instance does not have/may not have an Internet connection and therefore cannot reach the TL server, the following workaround is recommended:
- Install a Sign Live! C.C.C-TL instance on a computer that is permitted to access TL servers on the Internet.
Version and patch level should match those of the Sign Live! C.C.CValidation instance. - Run on the Sign Live! C.C.C-TL instance to update the TL by using menu item Tools> Certificates> Update Trust Lists trigger the update of the trust lists manually.
The updated Trusted Lists (TL) can usually be found in the directory<SLCC_PROFILE>\tsl-
for example:C:\Users\<name>\.SignLiveCC_<version>\tsl - Replace on the Sign Live! C.C.C-Validation instance the contents of the directory
<SLCC_PROFILE>\tslthrough the TLs on the Sign Live! C.C.C-TL instance.
It is important that the replacement takes place completely! Everything else requires detailed know-how about the internal structure of the TLs. - Run on the Sign Live! C.C.C -Reboot validation instance.
This workaround uses internal Sign Live! C.C.C- Processes that you cannot influence.
Published to
18 January 2023
Depending on the characteristics of the license you are using, various actions may have restrictions. An example is the number of possible signatures per day. Once the limit is reached, the application continues to work very slowly.
- If the license you are using is not sufficient for you, please contact us via email about a license upgrade support@intarsys.de in connection.
- It is best if you let us know the license key you are currently using. You can find this under the menu item EXTRAS > LICENSE MANAGEMENT at the far right.
Published to
August 21, 2022
SignLive! CC creates log files. These help us to analyze errors and to help you quickly.
- Please post in SignLive! CC under Tools > Settings > Basic Settings the 'Log detail level' to 'All details'.
- Then please reproduce the error again.
Then go up Window > Show Log File.
A dialog with the log files appears. - Note the dialog heading. The path to the log files is displayed there.
- Go with that Finder > Go > Go to folder... Go to the folder shown and please send us all files with the extension ".log".
(Usually the log files are at/Users/<name>/Library/Application Support/SignLiveCC_<version>/filed.)
Published to
August 21, 2022
- Information about current versions (updates) is provided via newsletters. With the appropriate setting, an update check is carried out on the software side. The update is not installed automatically.
- Please note:
- If you use our software in conjunction with third-party software, please inquire advance at the manufacturer whether the update is to be carried out.
- The license is usually adopted within a master release. If you change the master release, a new license is required. Please note the version notes in any case.
- If you obtained the software from one of our partners, you will normally be informed accordingly by this partner.
- Since January 01.01.2019, XNUMX, our licenses have generally been so-called term licenses with a defined expiry date. Until this expiry date the update to the current version is free of charge.
- Please check whether the manufacturer of your card reader provides drivers for MAC.
The company's card reader drivers PURE SCT make here available. - You can find a list of the signature cards and card readers that we have tested in the Sign Live! CC data sheet.
Published to
August 21, 2022
A hotfix too Sign Live! C.C.C is provided as a ZIP file. To install the hotfix, the zip file must be extracted and the file(s) it contains copied to a specific directory. This FAQ explains how to get the files into the application directory of Sign Live! C.C.C be copied.
Please note the information in the hotfix about the directory to which the files should be copied.
- If open, exit Sign Live! C.C.C.
- For example, save the zip file on your desktop.
- Double click on the zip file. This is automatically unpacked and the unpacked folders and files are made available.
- Navigate to using the Finder Program, Mark your choiche Sign Live! C.C.C, Open the context menu and choose Show package contents. The “Contents” folder is displayed.
- Open the folders Contents/Resources.
- Copy the unzipped folders and files - which were made available in the previous step - into this folder or the folder specified in the hotfix.
- Starten Sie Sign Live! C.C.C New.
Published to
August 21, 2022
Please note that the driver software of the REINER SCT card readers may have to be updated as a result of MAC OS X updates.
Published to
August 21, 2022
Will the PURE SCT RFID convenience Card reader is used, when attempting to sign with a D-Trust card (from version 4.x) the error message “Card is not supported” occurs.
This can be remedied by turning off the RFID function directly on the card reader. To do this, use the arrow keys in the lower part of the number pad.
Published to
22. February 2024
If you are from Sign Live! CC click on the "Send current document" button, the file attachment is not created under Mac OS X.
This is because passing file attachments using the Mac OS X mailto protocol is not supported.
Solution:
Save file and attach later.
Published to
August 21, 2022
The card reader may be connected after the system has started, but not removed while the computer is running.
Published to
August 21, 2022
Occurs after updating MAC OS X after installing Sign Live! C.C.C the error message "Sign Live CC.app kann nicht geöffnet werden, da Apple darin nicht nach Schadsoftware suchen kann.",
can Sign Live! C.C.C can be opened as follows:
Right-click, select Open, confirm dialog.
Published to
August 21, 2022
The libfreetype.so library, which is required for displaying a document, is no longer included in the standard deb packages for Ubuntu 12.x. The package libfreetype6-dev must be installed afterwards.
Published to
August 21, 2022
The libpcsclite library, which is required for communication with a card reader, is no longer included in the standard deb packages for Ubuntu 12.x. The package libpcsclite-dev must be installed afterwards.
Published to
August 21, 2022
You can sign in ELSTER from various applications – for example ADDISON from the company “Wolters Kluwer”.
To do this, you need PKCS#11 drivers, which we can find in Sign Live! C.C.C provide.
You can find them in Sign Live! C.C.C via menu item Tools> Settings> Libraries> PKCS # 11.
Please note:
- An RSASignature card – for example the D-TRUST – is required. Signature cards that use ECC (Elliptic curve cryptography) are not supported by this library.
- Sign Live! C.C.C is required at least version 7.1.9.
Please configure the driver directly in the application to be used.
Please note that you are alone with Sign Live! C.C.C cannot sign in ELSTER.
Published to
18 January 2023
You probably put one Signature card the D-TRUST. There are several certificates on the D-TRUST card. Among other things, a certificate for the qualified signature and one for advanced signature/authentication.
In the account query, the certificate for authentication used and therefore also requires the PIN for authentication.
If you get the error message "Incorrect PIN" when you query your account, you probably entered the PIN for signing instead of the PIN for authentication. Please note that these two PINs are usually different.
Tip:
If you entered the wrong PIN more than 3 times, it was blocked. It is also possible that this has not yet been activated in principle.
In Sign Live! C.C.C you can use the menu item Tools> Smart Card Tools > PIN Management initialize (put into operation) or reset (a blocked PIN) the PINs.
In both cases, please note the PIN letter from the card manufacturer.
Note:
If the PIN of a D-TRUST card has been blocked due to multiple incorrect entries, it can maximum 10x on the old PIN be reset. Therefore, please make a note of the PINs you have assigned.
Published to
August 16, 2023
If you are doing the submissions in conjunction with Addison, you can go to the signature Sign Live! C.C.C use. You can purchase the software via our shop at https://www.chipkartenleser-shop.de/intarsys/sign-live-cc relate.
Unfortunately, if you want to make the submissions directly to ELSTER using the Elster Authenticator, our solution is not suitable.
In this case, please contact ELSTER directly.
Published to
18 January 2023
Sign Live! CC DATEV Edition
c
Expand all
C
Fold everything in
In cooperation with DATEV, the product Sign Live! CC DATEV edition
In the service video “Qualified digital signing of reports” The entire signature process is described in detail.
https://www.datev.de/web/de/service/self-service/servicevideo/berichte-qualifiziert-digital-signieren/
In addition to the signature software, you also need one Signature card and a card reader. The Signature card You can contact D-TRUST (Bundesdruckerei) at https://www.bundesdruckerei.de/de/bestellen acquire. We recommend as a card reader PURE SCT RFID convenience.
In order to ensure that the signature from the DATEV environment runs smoothly, it is essential that the Sign Live! CC DATEV edition is installed. Access to this version is set up individually.
The Order process of the Sign Live! CC DATEV edition you can under https://www.intarsys.de/DATEV-Edition-erwerben trigger.
Published to
August 24, 2022
For the signature from the DATEV environment compellingly can Sign Live! CC DATEV edition be installed. Otherwise, the proper execution of a signature from the DATEV environment cannot be guaranteed. The Sign Live! CC DATEV edition is available for download in a protected area on our homepage. The required access rights are set up individually. You will receive the information about this together with the license you have purchased.
You will be informed by email about the setup of your user data. If necessary, please also check your spam folder.
If you have not received access, please send an email to support@intarsys.de.
Published to
August 24, 2022
The Sign Live! CC DATEV edition is also available as a server version and is therefore executable under DATEVasp.
Unfortunately, only the software products provided directly by DATEV are available under DATEVsmartIT. Please inquire directly with DATEV whether Sign Live! CC DATEV edition part of it.
Published to
13 January 2023
Sign Live! CC Sparkasse Edition
c
Expand all
C
Fold everything in
Will in the Sign Live! CC SPARKASSEN edition If the validation report is generated with "extended options", the report can be attached to the original document. This causes the signatures to be marked with a red X. The message "The document has been changed since it was signed and is no longer valid" appears with the signatures.
According to the current PDF specification, the signature must be "broken" when the document is changed (page was attached). This behavior is correct according to the PDF specification.
Solution:
Do not attach the validation report to the original document, but save it as a separate file. The report is given the name by default <dateiname>.valreport.pdf.
Published to
August 21, 2022
When opening a bank statement in the Sign Live! CC Sparkasse Edition it will be validated automatically. This can take a few seconds. Once this process is complete, you will see on the left side of the screen on the "Sidebar" that the signature is valid.
If the message "Identity is unknown" appears in the validation report, you probably have an old version of the Sign Live! CC Sparkasse Edition in action. Please take one update to the current one Sign Live! CC SPARKASSEN edition before. You can obtain access to the current version from your Sparkasse.
Published to
August 21, 2022
The Sign Live! CC Sparkasse Edition was programmed exclusively for Windows.
The customers who use MacOS X are welcome to download the software for Mac at https://www.intarsys.de/dl_slcc download. Even without a license, Sign Live! CC signatures are checked.
There are the following differences to the Sparkassen edition:
- During installation you will be asked for a product key. This query can be skipped.
- The test reports as PDF can only with watermark and reference to a demo version be generated.
For the interactive verification of signatures, this solution can be used analogously to Sign Live! CC Sparkasse Edition should be used.
Published to
August 21, 2022
The Sign Live! CC Savings Bank Edition was commissioned by the DSGV (German Savings Banks and Giro Association) and made available to the business customers of the savings banks free of charge. It is intended for checking the signatures on account statements.
The license expires on June 30.06th. one year out. This requires an annual update. This update can easily be carried out over the existing installation.
You will receive the link to download the current version from your Sparkasse.
Published to
August 21, 2022
Needed to validate signatures Sign Live! C.C.C always current Root certificates that are at least available for the eIDAS-PKI Trust lists (Trusted List-TL).
Sign Live! C.C.C ships with a current set of root certificates at the time of publication. From time to time, trust centers use new root certificates. If we receive information about this from the trust centers, we will forward it to you via email. To do this, register for our newsletter.
In any case, you must ensure that Sign Live! C.C.C updated its root certificates. You can do this manually or automated carry out:
– For the workplace: Manual
This method is completely sufficient for normal installation at the workplace.
- Via menu item Tools> Certificates> Update Trust Lists trigger the update of the trust lists manually.
– For server installation: Automated
Especially in Server installations it makes sense to have the update triggered time-controlled. To do this, adapt the preconfigured service container:
- Via menu item Tools> Services> Service Container Management Configure the schedule of the "Trusted List Update Scheduler" service container and automatically trigger the update of the trust lists:


If the update is not possible or aborts with an error message, please check:
- The internet connection (proxy, firewall, ...).
- Whether the virus scanner deletes trusted lists downloaded from the profile directory. The profile directory is where the logs are stored. You can determine this using the menu option Window > Log File.
If the update is still not possible, please send a description of the error and the current log file an support@intarsys.de.
Published to
18 January 2023
Sign Live! cloud suite gears
c
Expand all
C
Fold everything in
Since January 1.1.2024st, XNUMX, Sign Live! CC in the signature process when using certain algorithms that they have expired. The background is that the signature creation settings are set to the outdated “SigG” testing standard.
Workaround: Reset this setting to “Standard”. Then the error should no longer occur.

If the problem persists, please send a description of the error and the current log file an support@intarsys.de.
The warning in the SLCC settings pages (Tools > Settings > Signature Devices > …) still appears.
The problem has been completely resolved by using the corrected version of Sign Live! CC 7.1.11.3 (for download) or from 7.1.12.
Published to
2 January 2024
a in Sign Live! cloud suite gears Version 8.10.0 (or older) documents signed with sign-me are displayed correctly, but during validation the message appears in the “Validity” area
- "The signature has been modified and is not valid. There are warnings."
Since July 2023, sign-me has been using the ECDSA signature algorithm to issue qualified EC certificates and to create signatures.
Signatures based on such a certificate and signed with Sign Live! cloud suite gears v8.10.0 or older are unfortunately permanently invalid.
As announced in our newsletters, it is therefore necessary to register on Sign Live! update cloud suite gears v8.10.1 or newer. This version has been available since March 2023.
Published to
August 25, 2023
The Tomcat standard configuration limits the maximum processing size of a POST request to 2 MB.
You can set this limit in <CATALINA>\conf\server.xml increase or cancel via the maxPostSize parameter (-1):
<Connector port="8080" protocol="HTTP/1.1"
connectionTimeout="20000″
maxPostSize="-1″
redirectPort="8443" />
Published to
August 21, 2022
For configuring the font in Sign Live! cloud suite gears - for example of signature fields - you need to know the exact name of this font. This is not always the display name or file name. To determine the correct name, look into the most recent gears log file and look for the desired font. Here using Arial Bold as an example:
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [TrueType]Arial Negreta
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [TrueType-postscript]Arial-BoldMT
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [TrueType-canonical]Arial,Bold
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [Any]Arial Negreta
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [Any-postscript]Arial-BoldMT
[22.07.2021-08:48:23.888][T][de.intarsys.cwt.font][...] font registry register C:/WINDOWS/Fonts/arialbd.ttf with [Any-canonical]Arial,Bold
[22.07.2021-08:48:23.889][D][de.intarsys.cwt.font][...] FontEnvironment loaded font 'Arial,Bold' from C:\WINDOWS\Fonts\arialbd.ttfBased on this example, the following "FontNames" can be used:
- Ariel Negreta
- Arial BoldMT
- Arial, Bold
Published to
August 21, 2022
When opening the Sign Live! cloud suite bridge from Sign Live! cloud suite gears a security question appears.
The message can be switched off for a specific protocol using a RegistryKey:
[HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Internet Explorer \ ProtocolExecute \ csbridge]"WarnOnOpen"=dword:00000000
or
[HKEY_CURRENT_USER \ SOFTWARE \ Microsoft \ Internet Explorer \ ProtocolExecute \ csbridge]"WarnOnOpen"=dword:00000000
For more information, see https://stackoverflow.com/questions/37702082/internet-explorer-or-edge-how-to-display-the-warning-that-appear-if-you-open-c?rq=1
Published to
August 21, 2022
This error appears z. B. when the "demo" profile has been deactivated.
In this case, the following entry in gears.properties is required:
spring.liquibase.enabled = false
Published to
August 21, 2022
The Sign Live! cloud suite gears viewer offers the ability to validate signatures. Current root certificates are required for the check, at least for the eIDAS-PKI Trust lists (Trusted List-TL).
Starting with version 8.10, Sign Live! cloud suite gears the ability to automatically update trust lists. Versions older than 8.10 must be migrated. For versions from 8.10 onwards, the necessary configuration may need to be added.
Please check your configuration and add if necessary
in ${cloudsuite.config.shared}\gears.properties
(under Windows normally: C:\ProgramData\cloudsuite\config\gears.properties)
the following lines and restart the application:
# Validation properties
# update trusted list every sunny day at midnight
trustedLists.update.cron=0 0 0 * * MON-SUN
Notes for more specific configuration.
Internet access is required to automatically update trusted lists.
If access is via a proxy, its data must be added to the Tomcat configuration. Information on this can be found in the gears manual chapter “Proxies – Outgoing”.
If the update is still not possible, please send a description of the error and the current log file an support@intarsys.de.
Published to
5 October 2023
c
Expand all
C
Fold everything in
proNEXT Archive Manager
c
Expand all
C
Fold everything in
As an IT system that preserves evidence, the proNEXT Archive Manager generates an electronic archive timestamp for archived documents and signatures and automatically re-signs the hash tree. The component offers all cryptographic extensions that are necessary to ensure the evidentiary value of electronic documents in accordance with Section 71a of the Code of Civil Procedure.
In addition to archives, the software can also be integrated into document management systems and/or e-file solutions and is certified according to BSI 03125 TR -ESOR.
Published to
24 November 2022
In accordance with the eIDAS regulation is the exact procedure for Germany in the technical guideline BSI TR 03125 (BSI TR-ESOR) clearly described. The BSI also publishes the security-relevant cryptographic algorithms in the form of a catalogue.
Published to
24 November 2022
So within the framework of long-term archiving can Maintaining the probative value of electronic signatures can be used, the point in time at which the signature was created must be documented conclusively in a suitable "evidence-preserving" IT system. This creates one Archive Timestamp and signs archived documents including their signatures again and again.
If a signed document is then requested from the archive system at any time and it is determined during verification that the cryptographic algorithms and parameters are no longer suitable for security, a Evidence document (with all timestamps generated to date) be proven that this electronically signed document was re-signed in a timely manner and its get legal usability at a hunt.
Published to
24 November 2022
In contrast to paper documents, the evidentiary suitability of electronically signed documents can "disappear" over time. The reason for this is the Loss of security suitability of cryptographic algorithms. In addition, the directories and documents required for checking certificates may no longer be available.
As a result, when archiving digital documents, it must not only be ensured that these can be found at any time are, but also for one possible evidence in court can be used.
Published to
24 November 2022
In the filing and storage of electronic documents and data is an implementation of Security goals at the highest possible level of technology necessary. The elementary evidence for this can be found in the Code of Civil Procedure (ZPO) § 371 a "Probative value of electronic documents". This is additionally supported by the Europe-wide applicable eIDAS regulation affirmed.
Published to
24 November 2022
c
Expand all
C
Fold everything in
Partner products
Software for bailiffs
c
Expand all
C
Fold everything in
If you want to sign from GVS a BNotK-Map for remote signature, it is necessary that you set this up accordingly in GVS.
You can see an example of the settings here.
Also, please make sure that Sign Live! C.C.C is entered as the software to be used.
Published to
June 28, 2023
If you use software from Baqué & Lauter GmbH as a bailiff and with Sign Live! C.C.C want to sign must in Sign Live! C.C.C a certain "Service" to be set up.
If during the installation of the bailiff software the software Sign Live! C.C.C was already installed, this service should have been set up automatically. Otherwise, this can also be done manually. You will find the corresponding instructions here.
Published to
9 January 2023
c
Expand all
C
Fold everything in
If you want to sign from GVS a BNotK-Map for remote signature, it is necessary that you set this up accordingly in GVS.
You can see an example of the settings here.
Also, please make sure that Sign Live! C.C.C is entered as the software to be used.
Published to
June 28, 2023
If you use software from Baqué & Lauter GmbH as a bailiff and with Sign Live! C.C.C want to sign must in Sign Live! C.C.C a certain "Service" to be set up.
If during the installation of the bailiff software the software Sign Live! C.C.C was already installed, this service should have been set up automatically. Otherwise, this can also be done manually. You will find the corresponding instructions here.
Published to
9 January 2023
Remote signature BNotK
c
Expand all
C
Fold everything in
The new BNotK Card will be in Sign Live! C.C.C supported from version 7.1.11.
In the future, the Federal Chamber of Notaries will issue its signature certificates via the remote signature service and no longer via a personal one Signature card provide.
Authentication for signature creation at the remote signature service is carried out using personal means Smart Card.
This requires a completely new approach to signature creation. This signature is not sent via the signature device “signIT smartcard CC” but rather via “signIT BNotK“. When signing, please select the appropriate signature device in the signature assistant. If your signature certificate is not available, please contact the support of the Federal Chamber of Notaries.
If you use a Reiner SCT card reader with an RFID function, be sure to switch off the RFID function so that there are no problems reading the authentication certificate that is on your card.
If you Sign Live! C.C.C from a specialist application, please inquire with the manufacturer whether the new signature device has been connected.
Published to
3 January 2023
When assigning individual PINs, it is permissible to assign a PIN with more than 8 characters.
When changing a PIN, the new PIN must have the same number of characters as the “old” PIN or more characters. For example, changing from a 9-digit PIN to an 8-digit PIN leaves the BNotK-Card not closed.
In Sign Live! C.C.C up to Version 7.1.11.1 is with a during the signing process BNotK-Card allows entry of a maximum of 8 characters.
Solution:
With update from Sign Live! C.C.C on the version 7.1.11.2 is a PIN entry from up to 16 characters is possible.
Check in Sign Live! C.C.C via menu item Help> About which version you are using and, if necessary, make an update.
Published to
March 23, 2023
After entering the PIN, the following message is displayed
Error message:
error 401 calling service 'https://logging.bnotk.de/auth/realms/RemoteSignature/auth/tls', Unauthorized
Possible Cause:
- Signature card blocked:
This error message appears when accessing the Signature card is blocked by another application, for example by GV software or online banking.
Solution: Please close the third-party application completely (system tray) and start the signing process again. - Can not reach server:
If the server of the Federal Chamber of Notaries is temporarily unavailable, the above message also appears. In this case, wait and start the signature process again later.
Error message:
No keys available
- In this case, please ask the support of the Federal Chamber of Notaries whether your signature certificate has been created and is available.
Published to
1. February 2023
Remote signature D-Trust Sign-Me
c
Expand all
C
Fold everything in
Sign me:
Typical questions about sign-me are answered in the FAQs from Bundesdruckerei answered.
Questions about a specific product:
You will receive information and FAQs about a specific product here.
For customers with personal access:
Here you can achieve that Service portal
Written inquiries:
You can use an online contact form on various topics here fill out, or send an email to support@bdr.de.
Via phone:
The Bundesdruckerei can be reached by telephone on 030 / 2598 3333.
Published to
8 April 2024
You can find various information about sign-me here.
Published to
August 21, 2022
Remote signature Swisscom AIS
c
Expand all
C
Fold everything in
You can create a TLS certificate for the Swisscom AIS service yourself.
You are responsible for the exact procedure here A detailed tutorial is available for download.
Published to
27 November 2023
Problems with the AIS signature service are often due to the following:
- Basic service problems
In this case, please check the Swisscom AIS status pagewhether such a problem exists.
There you will also find the link to Swisscom support. - TLS certificate has expired
A supports you in creating a TLS certificate Tutorial - Problems with incorrect, expired, no longer valid registration data
In this case, please first check whether you can generally sign:
- via SMS
- via MobileID
Very often, access problems are related to differences in the identification data collected and the one you provided.
You cannot check these differences! Only Swisscom has access to the recorded identification data.
In this case, you must contact Swisscom directly:
Direct access to Swisscom support:
- Website: Swisscom support
- E-mail: ent.incident-data@swisscom.com
- Telephone: +41 (0) 800 724 724, menu selection "Data Services", keyword "All-in Signing Service"
- Have your PRO number (PRO-00xx) ready. You can find it on the cover sheet of your service contract.
This speeds up processing considerably.
The following circumstances cause the deactivation of the identification data and make a new identification necessary:
- Identity document has expired.
- Change of mobile number.
- Change of authorization from SMS-TAN to Mobile ID app.
(for non-Swiss customers: the Mobile ID app MUST be activated before identification)
More information about the AIS service:
Published to
August 21, 2022
Card reader and signature pads
c
Expand all
C
Fold everything in
D-Trust has been issuing new generation 29.x signature cards since November 2023, 5.
You can sign with these signature cards
- in Sign Live! CC from version 7.1.12
- in Sign Live! cloud suite bridge from version 7.1.12
- in Sign Live! cloud suite gears from version 8.12.1
Restriction: PIN caching is not possible, i.e. PIN / CAN must be entered every time you restart.
The D-Trust card 5.x can only be initialized using the D-TRUST Card Assistant, which is provided to you by D-TRUST.
Our current recommendation:
- In parallel to the D-Trust card 5.x, D-Trust continues to offer generation 4.1 and signature cards Seal cards generation 4.4.
- Should your signature or Seal card still valid, there is no need for action. If your signature or Seal card is about to expire, we recommend that you take another one Signature card generation 4.1 or Seal card generation 4.4. These will be available until the end of August 2024.
Reasons:
- These signature cards have a new technical structure and therefore require adapted signature handling and, in some cases, a firmware update on the card readers used. The card readers recommended by D-Trust can be found on the D-Trust overview page under the heading “Available additional components”.
The card readers we tested are... data sheet documented. - In addition to the signature PIN, it is sometimes necessary to enter a so-called CAN. Please read carefully whether you are asked to enter the CAN or the signature PIN. Otherwise there is a risk that the card will be blocked accidentally due to incorrect entry.
- Hardware support for the PACE protocol is required for secure PIN entry on the card reader. The REINER SCT RFID comfort, for example, offers this.
- For card readers that only support the PACE protocol on the hardware side (e.g. REINER SCT RFID-comfort), PIN caching and insecure PIN entry are no longer possible. PIN caching is very often used in mass signature processes.
- Please note that a firmware update may be required to use REINER SCT RFID comfort. Instructions and the required driver can be found on the REINER SCT website here.
- Please only use the REINER SCT RFID standard after consulting with us. You can reach us by email at support@intarsys.de.
Published to
29 November 2023
For security-relevant applications - such as signature with Sign Live! C.C.C or Internet banking – card readers are divided into security classes.
To generate a qualified electronic signature, you need card readers of security class III. One of the distinguishing features of these devices is that they have a display in addition to the keyboard. There Sign Live! C.C.C has been certified by the BSI, we recommend card readers that also have this certification.
A list of manufacturers and the names of the card readers tested can be found in Sign Live! CC data sheet.
Published to
August 1, 2023
Sign Live! We test CC in all constellations with different signature cards and card readers. We use the latest driver software from the hardware manufacturer for these tests.
When in Sign Live! If the error message “Card reader with secure PIN entry required” appears during the signature process, a driver update is usually required.
Please ensure that your card reader driver software is up to date.
Please select your card reader type when selecting the product.
Published to
August 21, 2022
Sign Live! By default, CC only support card readers with secure PIN entry. As a result, when using a class 1 card reader (without keyboard and display) the error message "Card reader with secure PIN entry required" appears when creating a signature.
In order to be able to carry out a signature with a class 1 card reader, settings that deviate from the standard setting must be made.
To do this, proceed as follows:
• Open the Sign Live! settings dialog via "Extras > Settings". CC.
• Navigate to the “Signatures > Signature Devices > signIT” section smartcard CC”.
• Disable the option "Require secure PIN entry".
With the subsequent signature, the PIN is entered via a screen dialog or via the keyboard of your computer.
Published to
August 21, 2022
The ACS ACR38T USB reader, which is typically used in Switzerland with a SuisseID certificate, does not support secure PIN entry. This causes the error message "Card reader with secure PIN entry required" to appear when creating a signature.
In order to be able to carry out a signature with the USB reader, settings that deviate from the standard setting must be made.
To do this, proceed as follows:
• Open the Sign Live! settings dialog via "Extras > Settings". CC.
• Navigate to the “Signatures > Signature Devices > signIT” section smartcard CC”.
• Disable the option "Require secure PIN entry".
• Activate the option "Disable secure PIN entry".
With the subsequent signature, the PIN is entered via a screen dialog or via the keyboard of your computer.
Published to
August 21, 2022
To ensure that the CHERRY KC 1000 works with secure PIN entry, please follow the installation instructions carefully. If you have any questions, please contact the manufacturer.
Published to
August 21, 2022
Requirement:
- To properly operate a REINER SCT card reader, the installation of a device driver is required. This is available to you Page from REINER SCT ready for download.
- Basically, NONE is allowed when starting the computer Signature card stuck in the card reader.
Even if the Signature card If the card reader is not inserted into the card reader until the computer has already booted up, it may happen that the card reader is not recognized.
In addition, applications that also use (signature) cards (e.g. banking or booking systems) can block the card reader and no longer allow it.
In this case, disconnect the USB connection and restart the computer. It may be enough to activate the service for the task manager Smart Card restart.
Published to
August 21, 2022
D-Trust cards of generation 2023.x have been available since November 5. This card has a modified security system, so adjustments had to be made in our software for card readers with RFID functions.
The REINER SCT RFID standard with D-Trust card 5.x is used in this combination in Sign Live! Version 7.1.12 not recognized. If you use this combination, please write an email to support@intarsys.deso that we can provide you with a hotfix.
The REINER SCT cyberJack RFID standard card reader is currently not included in the data sheet and has not been released. It will be included in our tests from the next software version.
If necessary, please note the FAQs about the REINER SCT RFID comfort.
Published to
5 April 2024
D-Trust cards of generation 2023.x have been available since November 5. If the REINER SCT RFID comfort card reader is used to sign these new cards, a firmware update of the card reader is usually required.
You can find detailed instructions on the REINER SCT website here.
Please pay close attention to the display on the card reader, as in addition to the signature PIN, it may also be necessary to enter the CAN printed on the card.
Published to
8. February 2024
Basically it's with the card reader REINER SCT cyberJack one Secure PIN entry is possible provided the appropriate device driver is installed.
- When using a D-TRUST card 5.x
Appears at the signature in Sign Live! C.C.C with the D-TRUST card 5.x –Signature card and the card reader REINER SCT cyberJack one The note “Card reader with secure PIN entry required” must appear in Sign Live! CC via menu item
— Extras > Settings > Signatures > Signature devices signIT smartcard CC
the “PIN entry on secure terminal” checkbox must be DISABLED.
Please note that you will probably be asked for a CAN (printed on the card) and a SIGNATURE PIN.
Therefore, please read the instructions carefully.
Both entries must be made on the screen.
- When using a D-TRUST card 4.x or other signature cards
Appears at the signature in Sign Live! C.C.C with any Signature card and the card reader REINER SCT cyberJack one If you see the message “Card reader with secure PIN entry required”, the device driver has probably not been installed. This is available to you Page from REINER SCT ready for download.
Alternatively, Sign Live! CC via menu item
— Extras > Settings > Signatures > Signature devices signIT smartcard CC
the “PIN entry on secure terminal” checkbox must be DISABLED.
Then the PIN must be entered on the screen.
Published to
8. February 2024
REINER SCT has discontinued technical support for the REINER SCT e-com plus card reader. REINER SCT recommends switching to current card readers.
For a complete list of discontinued card readers, please visit the page of PURE SCT .
- Obsolete card readers will be used for Sign Live! C.C.C no longer tested.
- We pay in case of error no support for actions in Sign Live! C.C.C, which are carried out with obsolete card readers.
- There is still the possibility that Sign Live! C.C.C is functional with individual combinations of signature cards and obsolete card readers.
The following procedure led to success (no guarantee):
1) Uninstall the current Reiner SCT driver (cyberJack Base Components).
2) Install an older Reiner SCT driver. You can find the old cyberJack drivers here (6.10.8) or here (7.9.3)
Published to
August 17, 2022
The company REINER SCT has discontinued technical support for various card readers. Please see which card readers are affected Page from REINER SCT.
Discontinued card readers will no longer work with Sign Live! tested. This means that we cannot guarantee that discontinued card readers will work with the current cards used for signature.
An overview of the card readers we tested, in combination with different cards, can be found here Data sheet.
Published to
March 21, 2024
End devices such as signature pads and card readers are usually connected to the computer via USB. If the end device “suddenly” stops responding, it is likely that the energy-saving mode has been activated.
- You can disable the USB port power saving mode. You can find instructions here.
Published to
August 21, 2022
For smooth signing in Sign Live! C.C.C with the signature tablet signotec LCD Signature Pad Sigma (ST-BE105-2-FT100-B) the installation of a driver software is necessary.
Contrary to the information on the signotec website, the driver software for the above signature tablet is also available at Windows 10 are required for operation.
You can find the download of the driver software here. Please use “VCP Drivers”.
You may still need the FTDI driver, for example here available for download.
Operation on terminal server:
You can find detailed information and documentation on the operation of signotec signature pads on the Signotec website.
Published to
August 21, 2022
In particular, if card readers are connected via USB device servers, the network in between can cause the timeout of 5 seconds to be exceeded and Windows to Signature card logs out.
By adding / setting the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Calais\TransactionTimeoutDelay can be increased from the default of 5 seconds up to 60 seconds.
Published to
August 21, 2022
Signature and seal cards
c
Expand all
C
Fold everything in
You have a new one Signature card receive. Before you can use it to create a signature, it must be initialized, i.e. activated.
Depending on the trust center, individual PINs can or must be assigned during this process.
Depending on the trust center, you will receive it together with the Signature card – or with a separate PIN letter – an indication of which software you can use to initialize your card.
Please note:
After initialization, a confirmation of receipt must be sent to the trust center. This usually happens online. Only then will the certificate become yours Signature card added to the directory service and one with this Signature card The signature created can be validly validated.
Published to
August 24, 2022
Most signature cards come with a transport PIN. You must change this transport PIN to your personal PIN before the card can be used. Depending on Signature card These can also be several transport PINs, which should then all be changed one after the other.
Together with the Signature card or in a separate PIN letter you received information from the trust center about which software you can use to change the PINs.
You should write down the assigned PINs and keep them in a safe place. If you forget your PIN, the card can no longer be used - depending on the trust center.
Published to
August 24, 2022
If you have entered the PIN incorrectly several times, the Signature card blocked. Whether you can remove the lock depends on the one you use Signature card.
Some cards are blocked forever after entering the wrong PIN multiple times. In this case you will need a new (replacement) Signature card apply because the block cannot be lifted.
For cards for which you have also received a PUK from TrustCenter, you can unlock the PIN entry again by entering the PUK (reset).
Please be aware:
- As a rule, the reset can a maximum of ten times be performed.
- It is also common for the reset to reset the PIN to the “old” value. You should therefore write down the PIN.
- Those issued from January 2023 EHBA-TeleSec signature cards also behave in the same way.
With TeleSec signature cards, you assign a - usually 6-digit - SigG-PIN1 during initialization. You use this PIN for signature. You also assign a - usually 8-digit - SigG-PIN2. The PIN2 has the function of a PUK. You can find information about managing TeleSec PINs here.
Published to
August 24, 2022
Supplied with Sign Live! C.C.C There are a lot of certificates included. These are presented in groups. For the sake of clarity, it makes sense to have one create your own groupin which you can file your own certificates.
To get a certificate e.g. B. from one Signature card To make it available to third parties, save the certificate to this new group and export it.
How to export a certificate from your Signature card with the help of Sign Live! C.C.C:
- Starten Sie Sign Live! C.C.C and there EXTRAS > Certificates > Certificate management.
Editing icons are displayed in the top left. - Click on that first icon to create a new group to create.
(If the icon is not active, click a white area in the Filter window). - Give the new group one Namur (in the window on the left), e.g. B. "My certificates" and confirm with "Close".
- Select menu item again EXTRAS > Certificates > Certificate management.
Now select the new group "My Certificates".
(Ensure the card reader is connected to your PC and the card is inserted.) - Click on the icon "Add entry".
Select the “Certificate from one” action Smart Card Import” and “Next”.
The connection to the card is established and all certificates on the card are displayed. - Select the certificate you want off and "Next".
(If the recipient wants to insert the certificate into Adobe Reader, for example, in order to check your signature there in the future, the “qualified signature” certificate should be selected.) - In the next window you have the opportunity to do that Name certificate or accept the default identifier.
- In the next window, please mark the certificate as “trustworthy”.
- After "Finish" the selected certificate is entered in the group.
- Now you can use the symbol for "Export entry" save the certificate in any directory.
You can use the exported certificate e.g. B. make it available to a third person via email. The recipient must import the certificate into their software.
How to get a certificate in Sign Live! C.C.C Import is described in the FAQ “Importing certificates”.
Addendum:
All the necessary functions are available to you via the context menu (right mouse button).
Published to
August 24, 2022
How to import a certificate in Sign Live! C.C.C:
- Starten Sie Sign Live! C.C.C and choose
Menu item Tools > Certificates > Certificate management. - Highlight the group in which the new certificate should be included and select the second symbol (top left) to add the entry.
- Highlight in the next window the desired action and press "Next".
- Follow the further instructions.
Published to
August 24, 2022
The DGN has been sending out new signature cards since November 2023, which will be used from January 2024.
These new cards come with Sign Live! CC runs from version 7.1.11.x. If your new DGN card is not recognized, but the “old” card works without any problems, this is usually due to the card reader used.
The card readers we tested are... Sign Live! CC data sheet documented.
According to our knowledge, the new DGN card is not correctly recognized by old, discontinued card readers from REINER SCT. For a complete list of discontinued card readers, please visit the website PURE SCT . The model name is located on the back of your card reader.
Published to
18 December 2023
D-Trust has been issuing new generation 29.x signature cards since November 2023, 5.
You can sign with these signature cards
- in Sign Live! CC from version 7.1.12
- in Sign Live! cloud suite bridge from version 7.1.12
- in Sign Live! cloud suite gears from version 8.12.1
Restriction: PIN caching is not possible, i.e. PIN / CAN must be entered every time you restart.
The D-Trust card 5.x can only be initialized using the D-TRUST Card Assistant, which is provided to you by D-TRUST.
Our current recommendation:
- In parallel to the D-Trust card 5.x, D-Trust continues to offer generation 4.1 and signature cards Seal cards generation 4.4.
- Should your signature or Seal card still valid, there is no need for action. If your signature or Seal card is about to expire, we recommend that you take another one Signature card generation 4.1 or Seal card generation 4.4. These will be available until the end of August 2024.
Reasons:
- These signature cards have a new technical structure and therefore require adapted signature handling and, in some cases, a firmware update on the card readers used. The card readers recommended by D-Trust can be found on the D-Trust overview page under the heading “Available additional components”.
The card readers we tested are... data sheet documented. - In addition to the signature PIN, it is sometimes necessary to enter a so-called CAN. Please read carefully whether you are asked to enter the CAN or the signature PIN. Otherwise there is a risk that the card will be blocked accidentally due to incorrect entry.
- Hardware support for the PACE protocol is required for secure PIN entry on the card reader. The REINER SCT RFID comfort, for example, offers this.
- For card readers that only support the PACE protocol on the hardware side (e.g. REINER SCT RFID-comfort), PIN caching and insecure PIN entry are no longer possible. PIN caching is very often used in mass signature processes.
- Please note that a firmware update may be required to use REINER SCT RFID comfort. Instructions and the required driver can be found on the REINER SCT website here.
- Please only use the REINER SCT RFID standard after consulting with us. You can reach us by email at support@intarsys.de.
Published to
29 November 2023
About three days after you receive your Signature card received from D-TRUST, you will receive the PIN letter. In this PIN letter is next to the Transport PIN – which you need for initialization – also those Card PUK listed.
Please note:
- To put the card into operation, please only use the D-TRUST Card Assistant software, which is provided to you by D-TRUST.
- Please note before using the new card in connection with Sign Live! definitely the one further information.
Published to
28 November 2023
Answers to questions about D-TRUST signature cards can be found on the D-TRUST FAQ page.
In addition to general questions, the topics are also answered there Order, activation, blocking and SMS TAN procedure treated.
You will be taken to the D-TRUST website here.
Published to
August 14, 2023
About three days after you receive your Signature card received from D-TRUST, you received the PIN letter. In addition to the card PIN and transport PIN, this PIN letter also contains the Card PUK listed.
After entering an incorrect PIN three times, the card will be blocked. With the card PUK, you have the option of unlocking both the card PIN and the signature PIN.
Please note:
Unlocking can be done a maximum of ten times.
Unlocking the PINs on the old value reset. It is not possible to assign a new PIN. This means that if you forget your PIN, the card can no longer be used.
Published to
July 10, 2023
Bundesdruckerei (D-TRUST) has been issuing new signature cards since the beginning of October 2020. These can in Sign Live! C.C.C from version 7.1.6 be used.
What Sign LIVE! CC – Version you are using can be accessed via menu item Help> About check. An update may be required. If you Sign Live! C.C.C within or in combination with another partner software use, talk about installing the new version please beforehand with the manufacturer of this application. Please also note the version notes in advance.
As a user of the Sign Live! CC DATEV edition please make sure that you download the Sign Live! C.C.C DATEV Edition 7.1.6 must be registered on our website.
Published to
August 24, 2022
The PIN change mechanism from Sign Live! CC by default only allows numbers to be entered. The certificates of all German trust centers are designed in such a way that the personal PIN – to create a qualified electronic signature – must consist of numbers. The card readers certified by the BSI (Federal Office for Information Security) are also designed for entering numbers.
In contrast to German signature cards, signature cards from Switzerland allow an alphanumeric PIN. Because these PINs not suitable for creating qualified signatures according to SigG are, the use of alphanumeric PINs from Sign Live! C.C.C not offered. Would you still like to Sign Live! C.C.C to initialize (create individual PINs) Swiss signature cards, please proceed as follows:
- Turn the secure PIN entry. (Menu “Tools > Settings > Signatures > Signature Devices > signIT smartcard").
- Launch Sign Live! CC and select the menu item “Tools> Smart Card-Tools > PIN Management".
- Select the certificate you want and click on "Initialize".
- After reading the instructions in the next window, click "Complete".
- In the next window click on the switch "Input via keyboard".
- Open any text editor and enter the desired PIN.
- Highlight the entered PIN and copy it with the key combination CTRL+C.
- Switch to Sign Live! CC and paste the new PIN into the “new PIN” and “repeat new PIN” field using the key combination CTRL+V.
- Confirm your input by clicking on the "Finish" button.
Please note:
- That this only applies to signature cards from Switzerland, since German signature cards only allow numbers.
- Before you use alphanumeric PINs, you should consider that the creation of qualified signatures according to German SigG is not possible with alphanumeric PINs.
Published to
August 24, 2022
The healthcare professional cards G2.x from D-TRUST, Telesec, DGN and medisign are provided by Sign Live! CC from version 7.1.11.x supported. If necessary, please make an update and pay attention to the version notes.
We do not assume any liability for other medical profession IDs. But that doesn't mean they don't work.
Published to
August 24, 2022
If you are applying for a new card Signature card If you use your passport, sometimes certain data will not be accepted correctly.
In this case, select "ID" instead of "Passport" when selecting the ID card type. Then it should work.
Published to
August 24, 2022
Before using a TeleSecSignature card this must be initialized. The transport PIN is converted into an individual PIN.
- For this purpose, TeleSec provides you with software that supports you in managing certificates and PINs. You will find these here under “TeleSec CardManager.net”. The “TeleSec CardManager.net” is also suitable for resetting blocked PINs.
- Alternatively, you can use the “Software – Toolbox SignLive!”, which is also available to you here is available for download.
We do not provide support for either program. Please contact the TeleSec support.
Published to
19 October 2023
After the PINs for the Signature card have been set, a confirmation of receipt must be sent to TeleSec. Only then will the certificate be included in the directory service and can be validly validated.
For confirmation of receipt and other related services Signature card has the Telesec here a page set up.
Published to
19 October 2023
If you use the TelesecSignature card and a contactless reader (for example REINER SCT cyberJack RFID comfort), errors can occur if the Signature card in the contactless (rear) slot. The TeleSec card has limited functionality via contactless connections, but SigG PINs 1 and 2 cannot be used.
In this case, please use the front slot.
Published to
August 24, 2022
On a TeleSecSignature card There are 4 PINs, all of which you assign individually. Please make a note of all assigned PINs and keep this information in a safe place.
SignG PIN 1 (for qualified signature) – with this PIN you execute the qualified signature.
Global PIN 1 (for encryption and authentication) – you use this PIN to encrypt documents or log on to a portal.
SignG PIN 2 and Global PIN 2 you will need if you have blocked the respective PIN 1 by entering it incorrectly several times. This is comparable to a PUK, with the difference that you also assign the PIN2 yourself.
So why is it that PIN 2 cannot be initialized with the message “The card reader... is not supported”?
The security of card readers is divided into classes. The card reader you are using probably has a maximum of security class II and supports it in combination with the one you are using Signature card save secure PIN entry.
Solution:
Please disable in Sign Live! C.C.C via menu item EXTRAS > Settings secure PIN entry.
We strongly recommend using a card reader certified by the BSI (Federal Office for Information Security). The card readers we tested can be found in our data sheet.
Published to
August 24, 2022
With a TeleSec card, you assign one when you initialize (activate) the card SigG PIN2 and Global PIN2. These have the function of a PUK.
To restore the PIN that was blocked due to multiple incorrect entries, start Sign Live! CC and select the menu item “Tools> Smart Card-Tools > Reset PIN”. Follow the instructions in the dialogs.
If you have not assigned a PIN2, it is Signature card blocked.
Published to
August 24, 2022
General topics
eIDAS regulation
c
Expand all
C
Fold everything in
On September 01.07.2017st, XNUMX the eIDAS regulation in force. The TRUST centers (Telesec, D-TRUST etc.) have therefore adjusted their certificates. In order to be able to continue validating these certificates successfully, in Sign Live! C.C.C an update to version 7.x is required.
Published to
August 24, 2022
A trust service is loud eIDAS regulation, Article 3 (16), an electronic service that is usually provided for a fee and is responsible, among other things, for the generation of the seals, signatures and website certificates. A qualified trust service is a trust service that meets the relevant requirements of the eIDAS regulation fulfills Article 3 (17) and is checked every two years in a complex procedure by an accredited conformity assessment body and the result is communicated to the responsible supervisory authority (BNetzA or BSI). The status as a qualified trust service provider can be verified throughout Europe via a trust list and a seal of quality. The German trusted list is on the EU Trusted List Browser website https://webgate.ec.europa.eu visible.
Published to
August 24, 2022
The eIDAS regulation (eIDAS stands for "Electronic Identification And Trust Services") is a regulation on electronic identification and trust services for electronic transactions in the 28 member states of the European Union. eIDAS represents a real legal innovation, the stated purpose of which is to encourage the development of digital applications in Europe. The eIDAS is divided into two main points:
• Electronic identification
• Trust Services
• Electronic signature / remote signature
• Electronic seals / remote seals
• Electronic timestamps
• Audit and Preservation Service
• Electronic registered mail and delivery service
• Website authentication
The new EU regulation enables a new, simplified procedure for personal electronic signatures. The qualified certificate does not necessarily have to be on one Smart Card but can be stored in a secured IT environment of a qualified trust service provider. This means that the electronic signature can also be triggered remotely, for example with mobile devices such as tablets and smartphones.
With the publication of the eIDAS Implementation Act on July 28, 2017 in the Federal Law Gazette, it came into force on July 29, 2017. At the same time, the Signature Act of May 16, 2001 and the Signature Ordinance of November 16, 2001 are no longer in force. The core of the eIDAS Implementation Act is the Trust Services Act (VDG). This transposed the EU regulation eIDAS into national law.
Published to
August 24, 2022
The eIDAS regulation simplifies existing signature procedures with the introduction of a so-called remote signature. The electronic signature can be done without Signature card and trigger the reader, for example via mobile devices such as smartphones or tablets. With this new process, the user's private signature key is stored on a highly secure server (hardware security module) of the qualified trust service provider. A qualified signature is generated by the user via two-factor authentication (TAN-SMS).
Published to
August 24, 2022
The eIDAS regulation defines two different signature types - advanced and qualified. Advanced and qualified services differ in their legal meaning. If, for example, the written form is required in Germany, this can only be fulfilled with a qualified electronic signature. If the assessment of evidence is of interest for a business transaction, the following applies to qualified certificates:
- ZPO §371a (1): The regulations on the probative value of private documents apply accordingly to private electronic documents that are provided with a qualified electronic signature.
- eIDAS Art. 35 (2): For qualified electronic seals, the presumption of integrity of the data and correctness of the proof of origin of the data applies.
- eIDAS Art. 41 (2): Qualified electronic time stamps are presumed to be accurate of the date and time indicated therein and of the integrity of the data associated with the date and time.
- eIDAS Art. 43 (2): For qualified electronic registration and delivery services, the presumption of integrity of the data and the correctness of the proof of origin of the data and the time of transmission applies.
Published to
August 24, 2022
The eIDAS regulation places requirements on the trust service provider for seals, signatures and time stamps. The eIDAS does not make any direct demands on the signature application component. A publication of certifications or manufacturer declarations by the responsible supervisory authority is no longer possible.
However, with the M/460 of the EU [STANDARDIZATION MANDATE TO THE EUROPEAN STANDARDIZATION ORGANIZATIONS CEN,CENELEC AND ETSI IN THE FIELD OF INFORMATION AND COMMUNICATION TECHNOLOGIES APPLIED TO ELECTRONIC SIGNATURES] defines corresponding standards to be used in the development of Sign Live! are taken into account.
Published to
August 24, 2022
Encrypt and decrypt
c
Expand all
C
Fold everything in
In principle, the following applies to ALL signature cards (including follow-up cards!) from all signature card providers:
The “old” emails/documents were encrypted with your “old” public key and can therefore only be accessed with your “old” private key (the one on your “old” Signature card stored) can be decrypted.
You will receive a new key pair with a follow-up card / new card. This new key pair cannot be used for your existing emails / encrypted documents.
It is therefore advisable to use the “old” Signature card not to be disposed of.
The fact that a card has expired has occurred when decrypting DOCUMENTS with Sign Live! CC has no influence. The expiration date of the Signature card will be included in Sign Live! CC only checked at signature.
Published to
August 24, 2022
If a PDF document already has an internal signature, it is no longer possible to encrypt it using a password.
To effectively secure a document with a password, all of the payload it contains must be encrypted. This process inevitably compromises existing signatures.
Published to
August 24, 2022
Sign and validate
c
Expand all
C
Fold everything in
Users are increasingly noticing that documents signed with Internet-based signature service providers in combination with Sign Live! CC signed cannot be fully validated correctly. The following typical cases have occurred:
– docusign removes other existing signatures before creating a docusign signature.
– docusign and AdobeSign create final signatures that prevent adding more valid signatures.
- AdobeSign creates a certification signature as a completion signature after one or more confirmation signatures. This procedure contradicts DIN/ISO 32000.
– AdobeSign currently (10.03.2023/XNUMX/XNUMX) uses a signature certificate whose validity status returns the status “unknown” via OCSP. This leads into Sign Live! C.C.C to the validation result "unknown".
We can only advise our customers to contact the creators of the signatures and work towards creating interoperable signatures.
The signature servicest d.velop sign Fortunately, it creates interoperable signatures.
Published to
March 16, 2023
PDF documents can be signed invisibly or visibly. In the case of the visible signature, the standard display is usually used, in which various data from the signature certificate are displayed in the defined signature field.
When displaying the signature individually, the signature date can be entered as a variable. The available alternatives are:
- system.millis:d = full case (2021_04_14-09_12_52_610)
- system.millis:ds = shorthand (14.04.21 09:12)
- system.millis:dm = middle notation (14.04.21/09/12 06:XNUMX:XNUMX)
- system.millis:df = long notation (Wednesday, April 14, 2021 09:12 CEST)
- system.millis:dd = Date Only (Wednesday, April 14, 2021)
- system.millis:dt = Time only (17:10 CET)
- system.millis:dd(YYYY) = Java Format (2016)
Please note that this is the system time at the time the signature field representation is generated. This can deviate from the signature time (e.g. from a time stamp).
The procedure for the individual display of the signature can be found in the tutorial. You can find this and other helpful tutorials here here.
Published to
August 24, 2022
For the packaging register must embedded Signatures in PAdES format be generated. PDF signatures are in Sign Live! CC created by default in the required PAdES format.
How to create an embedded signature in Sign Live! CC:
- Starten Sie Sign Live! C.C.C.
- Open the PDF file to be signed with Menu item File> Open.
- The signature process is carried out via the menu Tools> Signature Functions> Sign Document started.
- Select PDF signature – PDF internal signature according to PDF specification and press [Next].
- In the window Signature field position select the option Create a new signature field. After pressing [Next] the mouse pointer changes. Now, while holding down the left mouse button, open a field in the desired position and size on the PDF.
- As soon as you release the left mouse button, the window opens Signature field representation. Choose here Standard [Continue].
- Choose the signature device SignIT smartcard CC – Sign with Signature card and card readers at work [Further]. Please insert it now - if you haven't already done so Signature card into the card reader.
- Im Window Identity the card reader used and the certificate are taken from the Signature card displayed. Depending on the setting, multiple certificates can be displayed. Please select the certificate with the Purpose: qualified signature [Continue].
- The Window Attribute certificates can with [Next] skipped .
- You will now be prompted to enter your personal PIN. Enter the PIN on the card reader and confirm your entry also on the card reader.
- The successful signature is saved in Sign Live! C.C.C displayed in the left application window.
Please note that in order to create a qualified signature Sign Live! C.C.C must be licensed. A license for Windows or Mac OS can be obtained from our Shop be acquired.
Published to
August 24, 2022
The presentation of the signature can be designed individually. The procedure is in the tutorial "Design signature field display" described which you here available for download.
It is important to ensure that the last variable is in the window appearance contains a value. A newline as the last variable would lead to an error message (internal cryptographic library error).
Published to
August 24, 2022
For the qualified electronic signature you need in addition to the Software additionally a Signature card , and a Card reader.
You can obtain signature cards from trust service providers (VDA). The of Sign Live! C.C.C Supported signature cards and card readers can be found in our service description and system requirements.
Purchase the signature application software here Sign Live! C.C.C for different operating systems.
Published to
August 24, 2022
Documents are in Sign Live! C.C.C signed in “Trusted Mode”. This requires additional memory and can be problematic for large files Error message "...Java heap space" to lead
To sign large files, the Sign Live! C.C.C "Trusted Mode" can be switched off. When the file is opened, "All files (*.*)" is set as the file type.
How to sign large files with Sign Live! C.C.C:
- Via menu item "Tools> Settings> Trusted Mode" check box "Ensure document integrity" deactivate.
- Sign Live! Reboot CC.
- With menu item "File> Open" the file with Sign Live! C.C.C open. Please set the file type to “All files (*.*)”.
The file is opened (recognizable by the fact that the file name is displayed in the tab), but not displayed (message: The content of the document cannot be displayed because the document format is unknown). - Via symbol or menu item "Tools> Signature functions> Sign document" start the signing process. During the signing process, the file can be time-stamped if the time-stamp is set up. A PKCS#7 signature is generated.
Published to
August 24, 2022
Various providers of trust services (formerly Trustcenter) offer qualified time stamps with the highest evidential value for a fee.
Sign Live! C.C.C supports all common timestamps.
To use the timestamp you have to be in Sign Live! C.C.C perform two actions:
- Configure access to the timestamp provider
- Configure the signature to embed the timestamps.
The time stamp service is offered during the signature process.
Published to
August 24, 2022
We deprecated appending the signature file extension to a PKCS#7 signature Sign Live! C.C.C Version 7.x revised.
A file TEST.PDF is signed here as an example.
Via menu item Tools > Settings > Signatures > Signature Creation > Signature PKCS#7 The following settings are relevant here:
- Check box "Replace file extension instead of appending" aktiv: There will be a signature file according to the schema
<dateiname>.<dateierweiterung>.p7screated (TEST.PDF.p7s). - Check box "Replace file extension instead of appending" not active: There will be a signature file according to the schema
<dateiname>.p7screated (TEST.p7s).
Published to
August 24, 2022
What is a comfort signature?
In principle, a comfort signature is a small "mass processing" in which several documents are signed via a so-called service as soon as they are in the defined input directory. The signature PIN is entered once and the number of documents defined by the license is provided with an invisible signature. If this number is exceeded, another PIN entry is required.
Requirement:
- License for comfort signature is installed
- Multisignature card is available
facility in Sign Live! C.C.C:
- Via menu item Tools> Settings please by Signatures > Signature device > signITsmartcard the check boxes PIN entry required and PIN entry only via secure terminal deactivate.
- Allow PIN caching Please visit activate. Close the settings window with [OK].
- Via menu item Tools > Services > Service Container Management open this.
- Add a service container there with the green plus sign and select "File system" as the type [OK].
- In the "General container settings" Assign an ID (name of the service container) and press the green plus sign under Services.
- Select the service type "Signature creation“ and as a kind “Signature with Smart Card Session". [OK]
- With FSM monitoring you can define the directories. By default, the directories are in the directory
<benutzer>/<.SignLiveCC>/<name des dienstes>created.
You start the signature service with the green arrow.
Published to
August 24, 2022
Despite a valid signature, the validation result contains the information that no valid blacklist was found.
This can be fixed as follows.
- Schlieen Sie Sign Live! C.C.C
- Copy the file
<home>/demo/vmoptions/auth tunnelinginto the directory<home>/bin(home = installation directory). - Starten Sie Sign Live! C.C.C new and validate the document again.
Published to
August 24, 2022
You can see the time stamp in Sign Live! C.C.C in the Signature Browser sidebar.
- To do this, open the signed file with Sign Live! CC.
The default is Sign Live! C.C.C set in such a way that every document is already checked for a signature when it is opened. This check may take a moment.
- After the verification is complete, the signature overview is displayed in the left part of the window.
If this is not the case, the signature overview in the menu “View -> Sidebar -> Signature Overview” be switched on.
In the best case, all areas are marked with a green tick.
- One of the hooks is labeled “The timestamp is qualified and valid.”.
In addition, "Signed on:" is accompanied by the addition "(Source: time stamp)".
Published to
August 24, 2022
In order to validate, the application should specify that a block list check is carried out and – if this fails – an OCSP check (online status check) all certificates are to be checked for blocking. With this setting, Sign Live! C.C.C delivered.
- If a document is not validated despite having a valid signature, check the settings. To do this, open the settings dialog (menu item "Tools> Settings"), navigate to the "Signatures> Signature Validation> Certificate Validation " and answer the question "Which certificates should be checked using OCSP?" with "All certificates".
- Please make sure that the checkboxes "Restriction list check" and "Online status check" are activated.
Checking the signature again should produce a valid result.
Note:
Various trust centers have discontinued checking by blacklist and currently only use OCSP responders.
Published to
August 24, 2022
Signatures generated with intarsys products produce results in some validation tools that contain the terms "PARTIAL/FULL PDF" or "Empty Revision".
This is due to the fact that intarsys signature products integrate LTV* information into the PDF document as a new revision.
Many validation tools ignore this technical detail.
However, some validation tools alert the user to this fact by labeling the subject of the validation as PARTIAL PDF describe EU DSS demonstration WebApp or indicate that the document is a empty revision includes. These statements have no relevance to the validity of the verified signatures. The generated signatures are spec-compliant and even have to be generated that way if the LTV information is added after the signature.
*LTV – Long Term Validation
LTV information includes OCSP responses and/or revocation lists for the certificates required for an audit. This data makes it easier to check the signatures later and makes it possible for the check to be carried out even without a network connection.
Published to
18 January 2023
Needed to validate signatures Sign Live! C.C.C always current Root certificates that are at least available for the eIDAS-PKI Trust lists (Trusted List-TL).
Sign Live! C.C.C ships with a current set of root certificates at the time of publication. From time to time, trust centers use new root certificates. If we receive information about this from the trust centers, we will forward it to you via email. To do this, register for our newsletter.
In any case, you must ensure that Sign Live! C.C.C updated its root certificates. You can do this manually or automated carry out:
– For the workplace: Manual
This method is completely sufficient for normal installation at the workplace.
- Via menu item Tools> Certificates> Update Trust Lists trigger the update of the trust lists manually.
– For server installation: Automated
Especially in Server installations it makes sense to have the update triggered time-controlled. To do this, adapt the preconfigured service container:
- Via menu item Tools> Services> Service Container Management Configure the schedule of the "Trusted List Update Scheduler" service container and automatically trigger the update of the trust lists:


If the update is not possible or aborts with an error message, please check:
- The internet connection (proxy, firewall, ...).
- Whether the virus scanner deletes trusted lists downloaded from the profile directory. The profile directory is where the logs are stored. You can determine this using the menu option Window > Log File.
If the update is still not possible, please send a description of the error and the current log file an support@intarsys.de.
Published to
18 January 2023
When validating, the validity of certificates is usually first checked via OCSP query (online status query). This requires access to the Internet. Only if this query fails is a blocked list used for the check. However, blacklists are not made available by all trust centers.
Please check the following settings when installing Sign Live! CC:
- Tools > Settings > Signatures > Signature Validation > Certificate Validation:
Is the "Perform online status check" option enabled? - If you use a proxy to access the Internet, the access data must be configured under Extras> Settings> Internet connection.
If both settings are correct, please send a test document with the signature that showed the error during validation to for further error analysis Email to support. If this is not possible, carry out the incorrect validation again and send us the current log file.
Published to
August 21, 2023
Other
c
Expand all
C
Fold everything in
You can find tutorials on various topics here.
Published to
August 20, 2022
You can find the manufacturer's declaration and other interesting documents here.
Published to
August 24, 2022
What does Sign Live! CC implements the valid catalog of algorithms"?
An algorithm catalog defines which cryptographic algorithms are currently and for a future period considered secure. In doing so, it largely defines the security level of a PKI(1).
Until June 30.06.2017, 01.07.2017, the Signature Act and the Signature Ordinance (SigG/SigV) defined a PKI for qualified electronic signatures and required an algorithm catalog that was constantly updated. Since July XNUMXst, XNUMX, this has been done throughout Europe in the eIDAS regulation regulated.
The BSI (Federal Office for Information Security) creates the algorithm catalog based on a 7-year forecast. This means that the algorithms under consideration can be considered safe today and will most likely continue to be safe for at least the next 7 years. Very often these periods are extended every year. If it is expected that an algorithm will become unsafe, users have a warning period of 7 years. It has not happened since the existence of the SigG algorithm catalog that known attacks suddenly endanger the security level of crypto algorithms so much that a validity period had to be shortened.
Sign Live! CC implements the specifications of the algorithm catalog valid at the time of publication of the software.
What happens to the algorithm catalog through the implementation of the eIDAS-VO?
To the eIDAS regulation implemented in Germany, SigG/SigV will be replaced by the Trust Services Act and the associated ordinance at the end of 2017. An algorithm catalog is e.g. Currently not anchored in the eIDAS-VO. It is still unclear whether the EU administration will decide on the necessary rules at EU level by then or whether Germany will continue to stick to the German catalog as long as there is no EU catalogue. We will keep you informed on this topic.
(1) PKI = Public Key Infrastructure. For detailed information see https://de.wikipedia.org/wiki/Public-Key-Infrastruktur
Published to
August 24, 2022
You will be informed by us via newsletter about current versions. With the appropriate setting, an update check is carried out on the software side. The update is not installed automatically.
Since January 01.01.2019st, XNUMX, our licenses have been so-called runtime licenses with a defined expiry date. Until this expiration date the update to the current version is frees.
You have Sign Live! C.C.C before 01.01.2019/XNUMX/XNUMX acquired or no runtime license in use? Then please check whether you have concluded a maintenance contract with us. During the term of the maintenance contract, the update to the current version is free of charge.
Please note:
- If you use our software in conjunction with third-party software, please inquire advance at the manufacturer whether the update is to be carried out.
- The license is usually adopted within a master release. If you change the master release, a new license is required. Please note the release notes.
Published to
August 20, 2022
Please note:
If you have purchased the software used in your company via a subscription, as a runtime license (LTL) or have concluded a maintenance contract with us, you as a customer will receive important information exclusively - for example information about the free updates and bug fixes to which you are entitled. This information is communicated via newsletters. In that case, you should subscribe to the newsletter not to unsubscribe.
We received your e-mail address through a business contact with your company. At the end of each intarsys newsletter there is a section to unsubscribe from the newsletter. If you no longer wish to receive newsletters from intarsys in the future, please use the link in the newsletter and confirm it. You will then no longer receive any newsletters from intarsys.
Published to
August 24, 2022
Are intarsys products affected by CVE-2022-22965 "Spring Core Remote Code Execution Vulnerability Exploited In the Wild (SpringShell)"?
- https://spring.io/blog/2022/03/31/spring-framework-rce-early-announcement
- https://unit42.paloaltonetworks.com/cve-2022-22965-springshell/
intarsys products are not affected because
- only the intarsys product Sign Live! cloud suite gears spring used
- Sign Live! cloud suite gears is operated with Java 8
- Sign Live! cloud suite gears does not use spring-webmvc or spring webflux.
Published to
17 January 2023
Are intarsys products affected by the security vulnerability?
The BSI has the following security warning published.
The actual problem is explained in a PDF, which is continuously updated on the BSI website.
intarsys products are not affected by the security problem!
You can find the following intarsys products in the supported versions continue to operate without changes:
- Sign Live! C.C.C
- Sign Live! CC DATEV edition
- Sign Live! CC SPARKASSEN edition
- Sign Live! cloud suite bridge
- Sign Live! cloud suite gears
- Sign Live! cloud suite SDK
The Java library that is causing the problem is in these products not .
This also applies to the Archisoft product from FHI-SIT in versions 1.1.1.8 and 1.1.1.9, which is sold by intarsys.
Product-specific explanations
- In Sign Live! cloud suite gears Third-party products used up to version 8.7 are based on the critical Log4j version 2.14, but in the context of gears the dangerous library log4j-core-*.jar neither delivered nor used. There is therefore no potential risk.
- With Sign Live! C.C.C delivered Exampleimplementations (SDK / JMS) use Log4j version 1.x. These are only activated by calling the command line on the system and are also required a special Log4j configuration. They are therefore not viewed as a potential hazard.
Further safety information on the required basic components
tom cat 9 does not use Log4j in its basic configuration without standard and other web apps.
General safety information on the required basic components
Use the JVM in the required version (Java 11, SLcs gears: Java 8) at the most current patch level possible.
The Sign Live! CC / PDF / A Live! integrated JVM fulfills this (Java 11).
For Sign Live! cloud suite gears should be at least Azul JDK 8u312 + .
Further background information
Published to
17 January 2023
In the following, you will learn how to set up a remote connection to a JVM for as a function test via jconsole.
Security aspects are deliberately not taken into account. For this and more in-depth information, please see the linked information.
- Prepare JVM
Digression for Sign Live! C.C.C/ PDFA Live! /Sign Live! cloud suite bridge:
A complete JRE is required on the client side (where the intarsys product is operated) to use JMX.
The above products are delivered with reduced JREs. Therefore, it must first be ensured that the intarsys product starts with a complete JRE.
You can find information on this in this FAQ Starting SLCC with “my” JVM.
Configuration of the JVM for remote access
A port must be defined for remote access to the JVM and, for the sake of simplicity, security mechanisms must be switched off.
Add the following definitions to your Java configuration (any free port can be used as a port)-Dcom.sun.management.jmxremote.port=50999 -Dcom.sun.management.jmxremote.authenticate=false -Dcom.sun.management.jmxremote.ssl=false
For z. B. Sign Live! C.C.C put this data in the file C:\Program Files\Sign Live CC 7.1.7\bin\SignLiveCC.exe.vmoptions and restart the application.
Your JVM is now configured for remote access via JMX. - Establish a connection to the JVM with jconsole
Start the Java tool jconsole on the client.
You can find it in your Java installation (JDK) e.g. B. in the path C:\Program Files\Java\zulu11.48.21-ca-jdk11.0.11-win_x64\bin\jconsole.exe
Select the JVM to be monitored via the defined connection data:
acknowledge the warning
... and you get access to the JVM. After switching to the MBeans tab, read e.g. B. the current license status:
More Information
- The version of the client JDK is independent of the one used in the intarsys product.
It must be a JDK. - When accessing from localhost, there is no need to define a port and switch off security.
More detailed information
Published to
August 20, 2022
According to the GDPR, all persons involved in the signature process must be informed about which of their personal data is stored in the signature. Sign Live! C.C.C offers the possibility to display all information stored in the certificate before creating a signature. After the signature, all information stored in the signature can be viewed.
Should a VDA (VtrustDservicesAprovider) for testing services according to the eIDAS VO take over the test, these are in the sense of the BDSG / DSGVO (BandesDAtenSchutzGset / DAtenSchutzGperiodVregulation) processors and must provide corresponding AV contracts or agreements.
The trust services electronic seal and electronic time stamp remain unaffected by the GDPR.
Published to
August 24, 2022
You will certainly understand that we cannot provide any information about the beA. Current information can be found on the website of the Federal Bar Association.
Published to
August 24, 2022
terms
c
Expand all
C
Fold everything in
A trust service is loud eIDAS regulation, Article 3 (16), an electronic service that is usually provided for a fee and is responsible, among other things, for the generation of the seals, signatures and website certificates. A qualified trust service is a trust service that meets the relevant requirements of the eIDAS regulation fulfills Article 3 (17) and is checked every two years in a complex procedure by an accredited conformity assessment body and the result is communicated to the responsible supervisory authority (BNetzA or BSI). The status as a qualified trust service provider can be verified throughout Europe via a trust list and a seal of quality. The German trusted list is on the EU Trusted List Browser website https://webgate.ec.europa.eu visible.
Published to
August 24, 2022
A distinction is made between different forms of electronic signatures, all of which are legally binding, but have different probative value and are therefore suitable for very different areas of application.
- The simple signature does not make any requirement to identify the person signing the data. There is also no requirement as to how the signed data is linked to the signature and therefore no prescribed way of checking this. The digitized lettering of a signature (e.g. using a signature pad) represents a simple signature, as does the use of an e-mail footer. Simple signatures can be enhanced by using a certificate to create them. This allows the integrity of the data to be checked. If a qualified seal is used for this, the assessment of evidence according to eIDAS Art. 35 (2) applies.
- The advanced signature is generated by means that the signer can maintain under his sole control. The requirements for the identification and storage of the key used are publicly stored in the Certification Practice Statement (CPS). All important information about the Certificate Authority (CA), its guidelines and procedures are summarized in the CPS. This results in a clear assignment of the owner. The integrity of the document can also be ensured by signing with such a certificate.
- Within the qualified electronic signature the owner of the signature can be clearly and securely assigned, since the identification takes place, for example, via PostIdent, VideoIdent or the online ID function (eID). A qualified certificate is used, which was issued by a trust service provider confirmed in accordance with eIDAS. Only this type of signature complies with the written form BGB §126a and is after ZPO §371a proving.
Published to
August 24, 2022
It should be possible to check whether a signature is valid, i.e. valid, even after many years. In order to be able to check a signature again, several pieces of information must be available:
- Was the end user certificate used valid at the time it was used?
- Was the issuing CA (Certificate Authority) of this certificate trustworthy and the root certificate valid at the time the end user certificate was created?
- What was the quality level of the certificate used? Basic, advanced or qualified?
To confidently answer these questions, a validation application such as Sign Live! several exams. An important aspect of this check are revocation checks using OCSP (Online Certificate Status Protocol), ie queries to the trust service provider (VDA) that issued the end user certificate used. In order for these OCSP queries to be carried out, this service must be made available online by the VDA (directory service). The replies from the VDA are in turn signed by the latter so that the trustworthiness can be checked and thus ensured. This is then done in turn with the inclusion of OCSP queries. International standards (ETSI) regulate how this is to be done in full. At the end of these queries, the validation application can then provide a trustworthy status of the end user certificate used.
But what if the necessary directory service is temporarily or permanently unavailable? A temporary disruption can occur if the required directory service is simply not available online. Or what if this was switched off by the VDA being discontinued? The central deletion of information after the retention periods have expired also represents a cut. The end user certificate used cannot be checked in such cases and therefore the complete signature check does not lead to a clear result.
LTV signatures are different. With this type of signature, all required information is embedded in the signature, again according to international standards (ETSI). In the case of PDF documents and signatures, this is technically regulated, for example, by the PAdES standard (ETSI EN 319 142) in the context of the PAdES-B-LT profile.
The necessary information can be embedded both during signature creation and later during validation. However, it is rare for the validation information to be embedded during signature creation, as this would slow down the entire process. In addition to the time required to create the signature, the time for validation would also be added. It is therefore a good idea to enrich the LTV data during validation before archiving. From this point on, the signature is always checked offline and takes place without access to the directory service. A test is therefore independent of the availability of this service, regardless of the reason why it is not available.
Does the LTV signature do even more?
How the validity of certificates is checked is based on different models (chain, shell or modified shell model). These different models also make sense for the different uses of certificates. The validity of an SSL certificate should be checked differently in the browser than a certificate that was used to sign documents that have to be verifiable for decades.
Let's take Adobe Reader as an example. Adobe Reader will no longer classify a signature as trustworthy after the end user certificate used has expired, even if the signature was made during the validity period.
This behavior can be avoided by the LTV signature if the LTV signature is done before the expiration date. With the timely LTV signature, the Adobe Reader tick stays green and the signature continues to be positively checked - permanently. This is an important step on the way to greater user acceptance of the signature.
How to create an LTV signature with Sign Live! CC generated?
Published to
August 24, 2022